Introduction
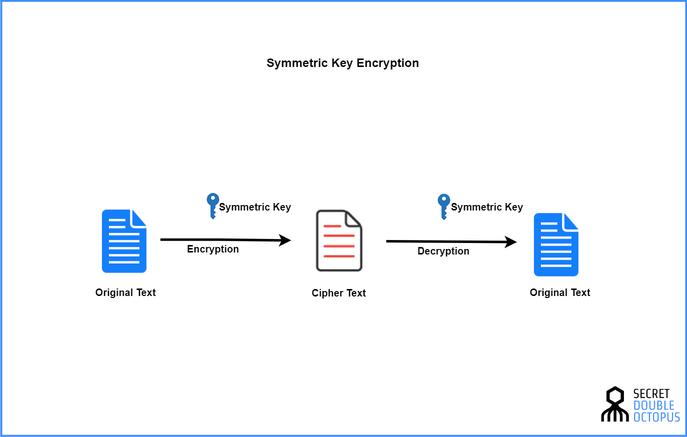
Symmetrical or Secret Key Password has been used for thousands of years, which includes any encryption form, where the same key is used for encryption and is also used for decryption. Text. One of the simplest forms is often referred to as "Caesar" password - It is said to be a method of juliuscaesar to hide messages - the process is simple, that is, moving the alphabet in a direction or reverse direction. The HAL / IBM example provided in Part 1 is this form, and its key indicates to decrypt the letter forward one. In this normal example, the decryption key is a mirror image of an encryption key, not its replica, but this does not harm the confidential level as a symmetric mechanism.
Arrangement
variants of this simple solution relate to the use of any sorted alphabet, which is the same length as the alphabet for the plain text message. In this case, the key may be a long sequence consisting of numbers, for example: 5, 19, 1, 2, 11 ... indicating that A should be mapped to E, B is S, C is A, D is B. , E is K, etc. - may also be a large number of original solutions that include letters (assumables) are selected from the sentence of a particular novel.
Of course, such a system is extremely fragile, and modern systems use a complex algorithm based on a difficult mathematical problem, and thus tends to be extremely strong.
The process of asymmetric cryptography has a common element, and it is almost never shared private key. Different from non-symmetric cryptography, symmetric cryptosystems typically need to share keys in a restricted group and maintain their confidentiality. For a person who views data encrypted with symmetrical password, if there is no access to the key for encrypted data, he is completely impossible to view encrypted data. If such a secret falls into the hand of the bad guy, it will immediately completely endanger the security of the data encrypted using the key. Therefore, the content shared by all systems in this group using the secret key is the difficulty of key management, which will be discussed in more detail in the characteristics of the actual problem (immediately after this series).
Password length
The key typically mentioned has a specific bit length, such as 56 bits or 128 bits. These lengths are the length of the symmetric key password, and the key length of at least private elements in the non-symmetric key password is quite long. Moreover, there is no correlation between the two groups of key lengths, unless it is even for a given system, the security level provided by a given key length is reached. However, Philzimmermann, very efficient and important package - the founder called "PRETTYGOODPRIVACY, PGP)", proposes 80-bit symmetrical keys, currently in terms of security and 1024-bit asymmetric key approximation To get the security of 128-bit symmetric keys, you may need to use a 3000-bit asymmetric key. Some people will definitely compare some of them, (no doubt) or even attempts to objections.
However, in any specific group, the length of the key used is usually an important factor when determining security. Moreover, the key length is not linear, but is doubled for each addition. The second second party is four, three times is eight, four times is sixteen, and push it accordingly. GigaGroup provides a simple metaphor that makes it possible to make a swimming pool to accommodate all 56-bit key combinations for all possible 40-bit key combinations, and accommodate all possible 128-bit key combinations The volume will be roughly equivalent to the volume of the Earth. A 128-bit value represented by decimal is probably 340, followed by 36 zero.
The symmetric key method is much more than the non-symmetrical method, so the symmetric key method is the preferred mechanism when encrypting a large number of text. A password such as the DES (QV) is at least 100 times faster than the asymmetric password RSA in the software (discussed in the characteristics of the non-confi system), and may be 10,000 times when implementing the dedicated hardware. The secret key is best suited for protecting data in a single user or a small group environment, usually by using password implementation. In fact, as the most satisfactory methods widely used in other parts, the most satisfactory ways that are widely used, are often combined with symmetrical and non-true systems.
Symmetric password type
Now, you will use the block password (streamCIpher) to implement the symmetric password, we will discuss these two passwords. This feature is also considered to be called "MessageAuthenticationCode, Mac)" checksum mechanism. The MAC and message summary is completely different, and the message summary is used in the digital signature, which will be discussed in the characteristics of the asymmetric cryptography (Part 3).
Packet Password
The packet password converts the gentle text block of the fixed length into a long code, which is under the control of the secret. Decryption is achieved using a reverse transformation and the same key. For current many packet passwords, the packet size is 64 bits, but this is likely to increase.
Ming text messages are usually much longer than a specific packet size, and different techniques or modes are used. Examples of this method include: Electronics Coding (ECB), Password Packet Link (CBC) or Password Feedback (CFB). ECB uses the same key to simply encrypts one by one by one, in the CBC mode, each plaintext block "different or" operation with the previous secret block before encryption, thereby increasing complexity The degree can make some attacks more difficult to implement. "Output Feedback" mode (OFB) is similar to the CBC mode, but the amount of "different or" is independently generated. The CBC is widely used, such as in the DES (QV) implementation, and discusses in depth in the corresponding books of the technical aspects of cryptography. Note: The universal weakness of your own cryptographic system is to use some disclosed algorithms in a simple form, not to provide additional protection.
iterative packet password is a password having multiple cycles thereof, thus improving security. In each cycle, an appropriate transformation can be applied by using a special function to generate a subkey from the initial secret key. The additional calculation demand will inevitably affect the speed of the encryption, so there is a balance between security needs and execution speed. There is no free lunch in the world, the cryptography is also the same; some of the skills of applying appropriate methods are from what is the relationship between the weighing needs and their relationship with the demand balance.
The packet password includes DES, IDEA, SAFER, BLOWFISH, and SKIPJACK- the last one is the algorithm used in the US National Security Agency (NSA) "limiter chip.
Sequence Password
Compared to the packet password, the sequence password can be very fast, although some grouping passwords (such as CFB or DES in CFB or OFB) can be Operately operate as the sequence password. The sequence password acts on some small groups consisting of several bits, typically using a bit sequence called a key stream as a key to apply "different or" operations. Some sequence passwords are based on a mechanism called a "LinearfeedBackshiftregister, LFSR), which generates a binary sequence.
The sequence password is developed by a professional password, a Vernam password (one-timePAD). Examples of sequence password include RC4 and "SoftwareOptimizedEncryptionAlithm, Seal", and a special case of Vernam passwords or disposable passwords.
message authentication code
message authentication code (MAC) is not a password, but a special form of checksum (usually 32 bits), it is by using a secret The key is generated in conjunction with a specific authentication scheme and is attached to a message. The message summary is to generate and verify the generated and verified using an asymmetric key using a one-way hash function. Compared with both, the expected recipient needs to have access to the secret to verify the code.
